In today’s digital landscape, where our data lives in the cloud, it’s easy to think that the biggest threat to our details comes from malicious hackers. But here’s the kicker: the most meaningful vulnerabilities aren’t always the result of a grand scheme. Instead, they often stem from simple misconfigurations—those little oversights that can lead to catastrophic data breaches. Picture this: a door left ajar, a password not changed, or a setting incorrectly configured.Sounds harmless, right? Unluckily, in the world of cloud security, these small mistakes can have massive consequences.
That’s where Cloud Posture Management (CPM) comes into play. This innovative approach not only helps identify and rectify these misconfigurations but also empowers organizations to maintain a strong security posture in an ever-evolving threat landscape. So, if you’re ready to take control of your cloud environment and safeguard your data from unintended breaches, read on! We’ll explore how CPM can be your best ally in the fight against misconfigurations and help you secure your digital assets like never before.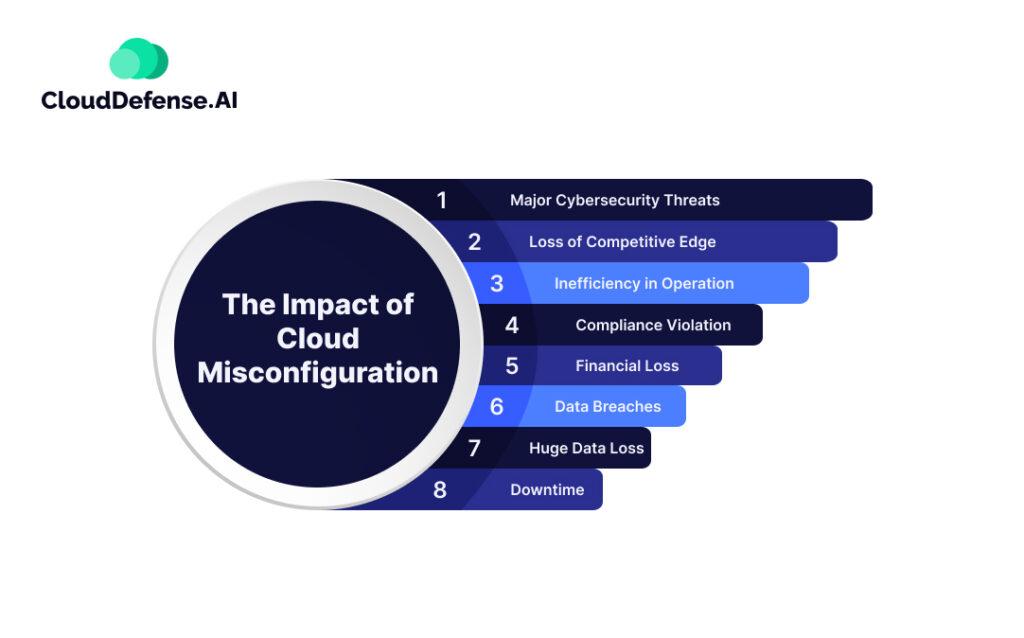
Understanding the Rise of Misconfigurations in Cloud Environments
In recent years, the shift towards cloud computing has transformed the way organizations operate, offering scalability and flexibility like never before. However, with this newfound freedom comes a significant challenge: misconfigurations. As businesses rapidly adopt cloud technologies, they often overlook the importance of proper configuration management, leading to vulnerabilities that malicious actors can exploit. This alarming trend is frequently enough likened to a data breach, as the repercussions of a single misconfiguration can be devastating.
So,what exactly contributes to this rise in misconfigurations? Several factors play a crucial role:
- Complexity of Cloud Services: Cloud environments frequently enough incorporate a multitude of services and configurations. This complexity can lead to oversight and errors during deployment.
- Lack of Training: Manny IT teams are not fully equipped with the knowledge of best practices for cloud security, resulting in unintentional missteps.
- rapid Deployment: The pressure to innovate and deploy quickly can cause teams to skip important security checks, leaving systems vulnerable.
Misconfigurations can take many forms, from leaving storage buckets exposed to the public to mismanaging IAM policies that govern user access. A recent survey revealed that over 60% of cloud security incidents are attributed to misconfiguration errors. This statistic is staggering and highlights the urgent need for effective cloud posture management solutions.
| Common Misconfigurations | Potential Impact |
|---|---|
| Publicly accessible storage | Data leakage and exposure |
| Weak IAM policies | Unauthorized access |
| Default security settings | Increased attack surface |
This is where cloud posture management (CPM) steps in as a crucial ally for organizations navigating the complexities of cloud security. By continuously monitoring configurations and providing automated insights, CPM tools help identify potential vulnerabilities before they can be exploited. Organizations can benefit from features such as:
- continuous Compliance Monitoring: Ensuring that cloud configurations adhere to industry standards and regulations.
- automated Remediation: Quickly addressing misconfigurations as they are detected, reducing the window of exposure.
- Visibility Across Environments: Offering a comprehensive view of all cloud resources and thier configurations, making management far more straightforward.
In a landscape where misconfigurations are becoming a leading cause of security incidents, leveraging cloud posture management tools is no longer a choice but a necessity. By prioritizing proper configuration management, organizations can bolster their defenses, prevent costly data breaches, and ultimately foster a secure cloud environment.

The Cost of Misconfigurations: why Ignoring Them Can Be Catastrophic
In today’s rapidly evolving digital landscape, misconfigurations pose a serious threat to organizations that overlook this critical aspect of their cloud security. A single misconfigured setting can open the door to vulnerabilities that cybercriminals can exploit, leading to severe repercussions. Businesses must recognize that these seemingly minor oversights can escalate into significant financial losses, reputational damage, and even legal ramifications.
Consider the following potential costs associated with misconfigurations:
- Financial Losses: The direct costs of a data breach can be staggering, including fines, legal fees, and compensatory damages.
- Reputation Damage: trust is hard to rebuild once compromised.Customers may flee, leading to a long-term decline in revenue.
- Operational Downtime: Remediation efforts can lead to extended periods of downtime, affecting productivity and service delivery.
to illustrate just how costly misconfigurations can be, recent studies have shown that organizations can spend millions of dollars recovering from a single incident. The average cost of a data breach in 2023 reached an all-time high, underscoring the urgent need for proactive management of cloud security settings.The following table outlines key statistics that highlight the impact of misconfigurations:
| Year | average Cost of a Data Breach | Percentage Due to Misconfigurations |
|---|---|---|
| 2021 | $4.24 million | 25% |
| 2022 | $4.35 million | 27% |
| 2023 | $4.45 million | 30% |
With such staggering statistics, it becomes evident that ignoring misconfigurations is not an option. Organizations must adopt a proactive stance towards cloud posture management to minimize risks associated with these vulnerabilities. By implementing comprehensive security protocols, conducting regular audits, and leveraging cloud posture management tools, businesses can identify and rectify misconfigurations before they lead to disastrous outcomes.
Transforming cloud security from a reactive to a proactive approach not only protects sensitive data but also preserves the integrity and trustworthiness of the organization. It’s about ensuring that every setting is configured correctly, every access point secured, and every potential vulnerability addressed. In a world where cyber threats are more sophisticated than ever, safeguarding against misconfigurations is not just a best practice; it’s a necessity for survival.
common Misconfigurations and How They Lead to Data Breaches
In the realm of cloud computing, misconfigurations are becoming alarmingly common, and they often serve as the gateway for data breaches. These oversights can take many forms, from overly permissive access controls to unsecured storage buckets. Organizations that overlook these details might potentially be unwittingly exposing sensitive data,leading to potentially devastating consequences.
One of the most prevalent issues is the use of default credentials. Many systems come with pre-set usernames and passwords that are well-known to attackers. When organizations fail to change these defaults, they leave the door wide open for intrusions. It’s a simple fix, yet one that many neglect, resulting in easy access for cybercriminals.
Another common misconfiguration arises from oversharing data. Often, companies grant broader access permissions than necessary, either to save time or due to a lack of awareness. This not only endangers sensitive information but also makes it easier for malicious actors to exploit the situation, especially when employees leave or change roles without their access being revoked.
Additionally, insecure cloud storage can pose a significant risk. many businesses utilize cloud services for their convenience but fail to implement proper security measures. For example, leaving cloud storage settings to “public” instead of “private” can expose critical data to everyone on the internet. This negligence can lead to extensive data leaks that could have been easily avoided with a few simple adjustments.
| Misconfiguration Type | Pitfall | Impact |
|---|---|---|
| Default Credentials | Easy access for attackers | Unauthorized data access |
| Oversharing Data | Broader access than necessary | Data leaks and exploitation |
| Unsecured Storage | Public access settings | Widespread information exposure |
These misconfigurations underscore the importance of cloud posture management. By continuously assessing and adjusting configurations, organizations can significantly reduce their risk of data breaches. Proactive measures,such as regular audits and the implementation of automated security protocols,can ensure that your cloud environment remains secure and compliant.
The Role of Cloud Posture Management in enhancing Security
In today’s rapidly evolving digital landscape, the security of cloud environments is more critical than ever. Despite the numerous advantages that cloud computing provides,misconfigurations remain a significant vulnerability. These missteps can lead to unauthorized access, data leakage, and ultimately, devastating breaches. This is where cloud posture management steps in, serving as a pivotal layer of defense.
Cloud posture management tools are designed to continuously assess and improve the security configurations of cloud infrastructures. By automating the identification of vulnerabilities, these tools ensure that organizations remain compliant with best practices and industry regulations. The benefits are substantial:
- Proactive Detection: These systems identify potential risks before they can be exploited.
- Real-time Monitoring: continuous oversight allows for immediate responses to any unauthorized changes.
- Enhanced Visibility: Users gain comprehensive insights into their cloud resources, making it easier to spot misconfigurations.
Moreover, integrating cloud posture management into your security strategy not only mitigates risks but also streamlines compliance efforts. Many organizations struggle with adhering to various regulatory frameworks, which can be burdensome. By leveraging automated compliance checks, businesses can effectively align their cloud usage with necessary standards, reducing the likelihood of costly penalties.
Consider a scenario where a growth team inadvertently exposes sensitive data due to a misconfigured storage bucket. Without a robust posture management solution,this issue might go unnoticed until it’s too late. With the right tools in place, alerts can be generated instantly, guiding teams to rectify the situation before it escalates.
| Feature | Benefit |
|---|---|
| Automation | Reduces manual errors and speeds up response times. |
| Policy Enforcement | Ensures configurations adhere to organizational standards. |
| Incident Response | Facilitates fast remediation of security incidents. |
Ultimately, cloud posture management is not just a tool; it’s a basic part of a robust security framework. By investing in these solutions,organizations are not only protecting their data but also fostering a culture of security awareness among their teams.Embracing cloud posture management is a proactive step towards ensuring that misconfigurations do not become the next vulnerability that leads to a data breach.
Proactive Strategies for Identifying and Resolving misconfigurations
In today’s rapidly evolving cloud landscape, misconfigurations have emerged as a significant threat, often serving as gateways for data breaches. To combat this, organizations must adopt proactive strategies that not only identify potential misconfigurations but also resolve them before they can be exploited. Here are several effective approaches:
- Regular Audits: Conducting routine audits of your cloud configurations ensures that any deviations from best practices are caught early. Automated tools can streamline this process, helping teams to focus on more complex issues.
- Policy Enforcement: Establishing and enforcing strict policies for configuration management is crucial. These policies should encompass guidelines for resource accessibility, usage, and security settings to guard against misconfigurations.
- Training and Awareness: Human error is frequently enough a leading cause of misconfigurations.Invest in ongoing training for your team to keep them updated on the latest cloud security measures and configuration best practices.
- Monitoring and Alerting: utilize comprehensive monitoring solutions that provide real-time alerts when configurations deviate from established norms. This allows for rapid identification and remediation of potential issues.
A well-designed Cloud Posture Management tool can be a game-changer in this regard. It provides visibility into your cloud environment, allowing for continuous assessment and remediation of configuration risks. Below is a simplified comparison of key features to consider when evaluating these tools:
| Feature | Description | Benefits |
|---|---|---|
| Automated Scanning | Regular checks for compliance against best practices. | Reduces manual effort and increases accuracy. |
| Real-Time Alerts | Instant notifications of any configuration changes. | Allows for immediate response to potential threats. |
| Reporting Tools | detailed logs and reports on configuration status. | Helps in compliance audits and strategy adjustments. |
By implementing these proactive strategies and leveraging the right tools,organizations can significantly mitigate the risk of misconfigurations leading to data breaches. The goal is to create a secure cloud environment where misconfigurations are identified and resolved before they pose a threat,ultimately enhancing your organization’s security posture.
Building a Culture of Security Awareness in Cloud Management
in the fast-evolving realm of cloud management,fostering a culture of security awareness is no longer optional—it’s essential. Organizations often overlook the human factor, focusing primarily on tools and technology.However,even the most sophisticated cloud solutions can falter if the team managing them lacks a robust understanding of security practices. To truly safeguard cloud environments, it’s vital to cultivate a mindset that prioritizes security at every level.
Here are some strategies to enhance security awareness within your organization:
- Regular training Sessions: Conduct frequent workshops and training modules to keep the team updated on the latest security threats and mitigation techniques.
- Phishing Simulations: Implement tests that mimic phishing attacks to raise awareness and improve response times among employees.
- Clear Interaction: Encourage open discussions about security concerns and share incident reports to highlight the importance of staying vigilant.
- Reward Programs: Recognize and reward employees who demonstrate exemplary security practices, fostering a sense of ownership and responsibility.
Additionally, integrating security into your cloud management processes is crucial. This means not just addressing security at the end of a project but making it an intrinsic part of the development lifecycle. Employ tools like Cloud Posture Management (CPM) to continuously monitor configurations and enforce security policies. By doing so, teams can quickly identify and rectify misconfigurations before they lead to data breaches.
A practical approach is to utilize a checklist for common misconfigurations in cloud environments. Below is a simple table outlining key areas to monitor:
| Configuration Aspect | Common Issues | Recommended Actions |
|---|---|---|
| Access Control | Excessive permissions granted | Implement Principle of Least Privilege |
| Storage Security | Publicly accessible buckets | Restrict access and enable encryption |
| Network security | Open security groups | Limit inbound and outbound traffic |
Ultimately, embedding a culture of security awareness not only protects your cloud infrastructure but also empowers employees to take proactive measures.When every team member understands the significance of their role in maintaining security, the organization as a whole becomes stronger and more resilient against potential threats. Reducing misconfigurations is a shared responsibility, and it starts with creating an informed, security-first mindset across your organization.

Choosing the right Cloud Posture Management Tools for Your Organization
When navigating the cloud landscape, organizations face a daunting challenge: ensuring their cloud environments are secure and compliant. Selecting the right Cloud Posture Management (CPM) tools is essential in mitigating risks associated with misconfigurations that can lead to data breaches. Here are several key considerations to keep in mind during your selection process:
- Comprehensive Visibility: Choose tools that provide a holistic view of your cloud infrastructure. They should be able to identify vulnerabilities across multiple cloud environments, offering insights into configurations, compliance status, and potential threats.
- Real-Time Monitoring: Opt for solutions that offer real-time alerts and monitoring capabilities.The ability to detect misconfigurations and policy violations as they happen allows for swift remediation, reducing the window of exposure to potential breaches.
- Integration Capabilities: ensure that the CPM tools can seamlessly integrate with your existing DevOps and CI/CD pipelines. This will not only streamline the deployment process but also enhance security without disrupting operational workflows.
- User-friendly Interface: A tool with an intuitive user interface will enable your team to analyze and respond to security alerts efficiently. Look for dashboards that visualize compliance status and alert you to high-risk configurations at a glance.
- Customizable Policies: Every organization has unique compliance requirements. Choose tools that allow you to customize security policies according to your specific needs and industry regulations.
In addition to selecting the right features, consider the scalability of the CPM tools. As your organization grows, the tools must adapt to accommodate increased workloads and complexity in your cloud infrastructure.Look for solutions that offer scalability without sacrificing performance or security.
Lastly,evaluate the vendor’s reputation and support options.Comprehensive documentation, responsive customer service, and a strong track record in the industry can significantly enhance your experience and ensure you get the most out of your cloud Posture Management tool. Choosing the right CPM solution is not just about safeguarding your data; it’s about establishing a robust security posture that evolves with your organization.
Here’s a quick comparison of some popular CPM tools that can help you make an informed decision:
| Tool Name | key features | Pricing Model |
|---|---|---|
| CloudGuard | real-time threat detection,compliance checks,integration with CI/CD | Subscription-based |
| Palo Alto Prisma | Comprehensive visibility,customizable policies,fast remediation | Tiered pricing |
| Aqua Security | Container security,serverless functions,runtime protection | Pay-as-you-go |

Real-World Examples of Misconfigurations and Their consequences
Misconfigurations in cloud environments can lead to devastating consequences, frequently enough resulting in significant data breaches that shake the foundations of trust between businesses and their customers. A notable example is the 2019 incident involving Capital One, where a misconfigured web request firewall allowed an attacker to access the personal information of over 100 million customers. This breach not only cost the company $80 million in fines but also severely damaged its reputation. It serves as a stark reminder of how an overlooked setting can have far-reaching implications.
Another eye-opening case is that of Tesla,which was also targeted due to a misconfiguration. In 2020, a former employee exploited an unsecured AWS S3 bucket, gaining access to sensitive company information. The breach was motivated by financial gain, highlighting how internal and external threats can exploit simple misconfigurations. Just a single misstep in cloud security can allow malicious entities to bypass safeguards and access confidential data, showcasing the urgent need for robust cloud posture management.
Even giants like Microsoft experienced a misconfiguration fallout. In 2020, an unsecured Azure blob storage instance exposed sensitive data from various companies, including those in the healthcare sector. The breach affected millions of records, prompting a slew of security audits and a reevaluation of cloud security practices. This incident illustrates that no organization is immune to the risks posed by misconfigurations, emphasizing the critical importance of implementing comprehensive monitoring and management strategies.
To provide a clearer understanding of the impact of misconfigurations,consider the following table that highlights some notable incidents:
| company | Year | incident | Consequences |
|---|---|---|---|
| Capital One | 2019 | Misconfigured firewall | $80 million in fines,reputational damage |
| Tesla | 2020 | Unsecured AWS S3 bucket | Data breach,internal security scrutiny |
| Microsoft | 2020 | Unsecured Azure blob storage | Exposure of millions of records,security audits |
These incidents not only highlight the repercussions of misconfigured cloud environments but also the necessity for organizations to adopt a proactive approach to cloud posture management. By implementing automated monitoring tools and regular audits, businesses can significantly reduce their risk of exposure. The stakes are high, and the cost of a misconfiguration can be far greater than the investment needed to avert one.

Best Practices for Continuous Monitoring and Compliance in the Cloud
In the fast-evolving landscape of cloud computing, maintaining a robust posture is essential to prevent misconfigurations that could lead to serious data breaches. Implementing continuous monitoring and compliance is not just a best practice; it’s a necessity for organizations that want to safeguard their assets. Here are several key strategies to consider:
- Automate Compliance checks: Leverage tools that can automate compliance checks against industry standards and regulations. This not only saves time but also ensures that your cloud environment is consistently aligned with compliance requirements.
- Real-Time Monitoring: Establish real-time monitoring systems to continuously assess the cloud environment. These tools can alert you to suspicious configurations or unauthorized access, allowing for immediate corrective actions.
- Regularly Update Policies: Compliance requirements can change frequently,so it’s crucial to regularly review and update your security policies. This ensures that your organization remains compliant and can rapidly adapt to new regulations or threats.
- Conduct Frequent Audits: Schedule regular audits of your cloud infrastructure. These audits help identify vulnerabilities and ensure that all configurations comply with organizational standards and regulatory requirements.
To further illustrate the effectiveness of continuous monitoring, consider the following table showcasing the most common misconfigurations in cloud environments and their potential impact:
| misconfiguration | Potential Impact |
|---|---|
| Open Storage Buckets | Data exposure to unauthorized users |
| Improper IAM Policies | Privilege escalation and data breaches |
| Unsecured APIs | Exploitation and unauthorized access |
| weak Security Groups | Increased attack surface and vulnerabilities |
By adopting these best practices, organizations can significantly reduce the risk of misconfigurations that lead to data breaches. The focus should be on creating a culture of compliance and security awareness among employees, as human error often plays a role in these incidents. Regular training and updates on the latest security protocols can empower your team to be the first line of defense against misconfigurations.
integrating cloud posture management tools into your compliance strategy can provide a comprehensive view of your cloud security. These tools can help visualize potential risks, assess compliance status, and guide remediation efforts—making it easier to maintain a secure cloud environment.With the right approach, organizations can not only prevent data breaches but also cultivate a resilient cloud infrastructure poised for growth and innovation.

Future-Proofing Your Cloud Security: The Importance of Ongoing Training and Support
As cloud environments rapidly evolve, so do the threats that target them. Organizations often find themselves grappling with the challenge of securing their cloud infrastructure while maintaining agility and innovation.A crucial aspect of strengthening cloud security lies in the commitment to ongoing training and support for all personnel involved in cloud management. This proactive approach ensures that teams are equipped to handle the complexities of cloud security, particularly in the face of misconfigurations that can expose sensitive data.
Regular training sessions should cover a range of topics, including:
- Best Practices for Cloud Configuration: Ensuring team members understand the foundational principles of cloud security to minimize errors.
- Incident Response Protocols: Preparing employees to respond swiftly and effectively to security incidents.
- Emerging Threats and Vulnerabilities: Keeping teams informed about the latest trends in cyber threats that specifically target cloud environments.
- Compliance Requirements: Familiarizing staff with regulations that govern data protection and privacy.
incorporating hands-on workshops and simulation exercises can significantly enhance the learning experience. These practical sessions allow teams to engage with real-world scenarios, fostering a deeper understanding of the potential consequences of misconfigurations. Additionally, organizations should consider leveraging external expertise to provide specialized training that aligns with industry standards and best practices.
Support is equally important in the quest for robust cloud security. Establishing a dedicated support team that is available to assist with cloud posture management can help alleviate the burden on individual employees.This team can provide:
- Real-time Monitoring: continuously assessing the cloud environment for potential misconfigurations and vulnerabilities.
- Guidance on Policy Implementation: Assisting teams in developing and enforcing security policies that align with business objectives.
- Regular Security Audits: Conducting audits to identify gaps in security posture and recommend improvements.
Ultimately, future-proofing your cloud security is about fostering a culture of continuous learning and support. By prioritizing ongoing training and establishing solid support systems, organizations can significantly reduce the risk of misconfigurations and enhance their overall security posture. As we navigate the complexities of the cloud landscape, the commitment to empowering teams through education and resources will be a decisive factor in safeguarding sensitive data.
Frequently Asked Questions (FAQ)
Q&A: Misconfigurations Are the New Data Breach: How Cloud Posture Management Helps
Q: What do you mean by “misconfigurations” in the context of cloud services?
A: Great question! misconfigurations refer to the incorrect or suboptimal setup of cloud resources, like servers, databases, and security policies. These issues can leave vulnerabilities open to attackers, and sadly, they have become one of the leading causes of data breaches today.
Q: How serious is this problem?
A: It’s incredibly serious! According to recent studies, misconfigurations account for a significant percentage of data breaches. With organizations increasingly moving their operations to the cloud, the risk of these mistakes inadvertently exposing sensitive information is higher than ever.
Q: So, how does Cloud Posture Management fit into this picture?
A: Cloud Posture Management (CPM) is like having a vigilant guardian for your cloud environment. It continuously assesses your cloud configurations, ensuring they adhere to best practices and compliance standards. CPM identifies and helps rectify misconfigurations before they become a costly breach.
Q: Can you give an example of how CPM addresses these misconfigurations?
A: Absolutely! imagine a company that inadvertently leaves a storage bucket publicly accessible. A CPM tool would flag this misconfiguration, alert the admin, and offer guidance on how to secure it. This proactive approach not only prevents data leaks but also saves the company from potential fines and reputational damage.
Q: I’ve heard that implementing CPM can be complex. Is that true?
A: It can seem daunting at first, but many modern CPM solutions are user-friendly and designed for seamless integration with existing systems. Plus, the benefits far outweigh the initial setup efforts. Investing in CPM means you’re prioritizing security, which ultimately protects your data and your business.
Q: How can organizations get started with Cloud Posture Management?
A: The first step is to assess your current cloud environment and identify any existing misconfigurations. From there, you can research CPM solutions that are compatible with your cloud provider. Many offer trial versions, so you can evaluate their effectiveness before committing.Q: Is it enough to just implement a CPM solution?
A: While implementing CPM is critical, it should be part of a broader security strategy. Regular training for your team, continuous monitoring, and a proactive security culture are just as critically important. Think of CPM as a vital component of your overall security architecture.
Q: What’s the bottom line? Why should organizations prioritize addressing misconfigurations?
A: The bottom line is simple: preventing misconfigurations is crucial for safeguarding your organization’s data and reputation. With cyber threats evolving, being proactive rather than reactive can save you from devastating breaches and financial losses. Cloud Posture Management is an essential tool in this fight—think of it as your first line of defense in today’s cloud-centric world!
Insights and conclusions
And there you have it! As we’ve seen, misconfigurations are not just minor oversights; they pose a significant risk to your organization’s data security. In the ever-evolving landscape of cloud computing, it’s essential to stay ahead of potential threats, and that’s where Cloud Posture Management (CPM) steps in. By proactively identifying and rectifying misconfigurations, you can fortify your cloud environment and safeguard your sensitive information.
So, why wait for a breach to happen? Embracing a robust CPM strategy is not just a smart move; it’s an essential step in protecting your business’s future. With the right tools and practices in place,you can ensure that your cloud is not just a powerhouse of innovation but also a secure fortress.Let’s take action now! Consider implementing Cloud Posture Management in your organization and join the ranks of those who are taking misconfigurations seriously. Remember, in today’s digital world, prevention is always better than cure.Let’s keep the data breaches at bay together!